by @"Alexandre Borges<em><img align="middle" alt="ace-icon.gif" class="image-4 jive-image" src="https://community.oracle.com/servlet/JiveServlet/downloadImage/15198/ace-icon.gif" data-mce-src="/servlet/JiveServlet/downloadImage/15198/ace-icon.gif"></em>"
Part 7 of a series that describes the key features of ZFS in Oracle Solaris 11.1 and provides step-by-step procedures explaining how to use them. This article focuses on sharing ZFS file systems using the SMB protocol. The first 6 parts were published in the old OTN web page.
Published December 2014
Introduction
Oracle Solaris 11 allows us to share a ZFS file system using the Server Message Block (SMB) protocol that was originally created by Microsoft. The procedure for sharing files using SMB is similar to sharing files using NFS and, honestly, it's so easy.
Here the fun begins.
First, we must install the SMB service on the system, if necessary. This service is installed when you install Oracle Solaris 11.1.
|
root@solaris11-1:~# pkg install service/file-system/smb
|
Next, create a file system with the share.smb, the SMB protocol mandatory locking (nbmand), and the cache client (csc) properties enabled:
|
root@solaris11-1:~# zfs create -o share.smb=on -o nbmand=on -o share.smb.csc=auto rpool/smb_example_1
|
The second file system will be created with almost the same configuration, but we will also accept guest clients by including the guestok property:
|
root@solaris11-1:~# zfs create -o share.smb=on -o nbmand=on -o share.smb.csc=auto \
-o share.smb.guestok=on rpool/smb_example_2
|
Then, check whether the sharesmb property is configured:
|
root@solaris11-1:~# zfs get sharesmb rpool/smb_example_1
NAME PROPERTY VALUE SOURCE
rpool/smb_example_1 share.smb on local
root@solaris11-1:~# zfs get sharesmb rpool/smb_example_2
NAME PROPERTY VALUE SOURCE
rpool/smb_example_2 share.smb on local
|
It's likely that the SMB server is not configured. Thus, this task must be done:
|
root@solaris11-1:~# svcadm enable -r smb/server
root@solaris11-1:~# svcs -a | grep smb
online 20:58:45 svc:/network/smb:default
online 20:08:26 svc:/network/smb/client:default
online 20:08:27 svc:/network/smb/server:default
|
After the SMB shares are configured, we can verify that the shares are offered by our system:
|
root@solaris11-1:~# zfs get share
NAME PROPERTY VALUE SOURCE
rpool/smb_example_1 share name=smb_example_1,path=/rpool/smb_example_1,prot=
smb,csc=auto local
rpool/smb_example_2 share name=smb_example_2,path=/rpool/smb_example_2,prot=
smb,csc=auto,guestok=true local
root@solaris11-1:~# cat /etc/dfs/sharetab
/var/smb/cvol c$ smb - Default Share
/rpool/smb_example_1 smb_example_1 smb csc=auto
/rpool/smb_example_2 smb_example_2 smb guestok,csc=auto
root@solaris11-1:~# share
IPC$ smb - Remote IPC
c$ /var/smb/cvol smb - Default Share
smb_example_2 /rpool/smb_example_2 smb csc=auto,guestok=true
smb_example_1 /rpool/smb_example_1 smb csc=auto
|
There's an interesting way to learn about the ACL information for a share such as smb_example_1:
|
root@solaris11-1:/ cd /rpool/smb_example_1/.zfs/shares
root@solaris11-1:/rpool/smb_example_1/.zfs/shares# ls -lv
total 1
-rwxrwxrwx+ 1 root root 0 Dec 5 15:58 smb_example_1
0:everyone@:read_data/write_data/append_data/read_xattr/write_xattr
/execute/delete_child/read_attributes/write_attributes/delete
/read_acl/write_acl/write_owner/synchronize:allow
|
Now, we will create a new user (with a password) and enable the new user to use the SMB share service:
|
root@solaris11-1:~# useradd borges
root@solaris11-1:~# passwd borges
New Password:
Re-enter new Password:
passwd: password successfully changed for borges
root@solaris11-1:~# smbadm enable-user borges
borges is enabled.
root@solaris11-1:~# smbadm lookup-user borges
borges: S-1-5-21-3351362105-248310137-3301682468-1102
|
SMB authentication can be enabled by inserting a new line at the end of the /etc/pam.d/other configuration file:
|
password required pam_smb_passwd.so.1 nowarn
root@solaris11-1:~# more /etc/pam.d/other
Copyright (c) 2012, Oracle and/or its affiliates. All rights reserved.
PAM configuration
Default definitions for Authentication management
Used when service name is not explicitly mentioned for authentication
auth definitive pam_user_policy.so.1
auth requisite pam_authtok_get.so.1
auth required pam_dhkeys.so.1
auth required pam_unix_auth.so.1
auth required pam_unix_cred.so.1
Default definition for Account management
Used when service name is not explicitly mentioned for account management
pam_tsol_account(5) returns PAM_IGNORE if the system is not configured
with Trusted Extensions (TX) enabled. In TX environments some PAM services
run in the Trusted Path where pam_tsol_account(5) isn't applicable so in
those cases, like gdm(1m) or xscreensaver(1), PAM stacks are delivered
in /etc/pam.d which exclude pam_tsol_account(5). pam_tsol_account(5) does
need to run in the Trusted Path for ensuring remote hosts connecting to the
global zone have a CIPSO host type.
account requisite pam_roles.so.1
account definitive pam_user_policy.so.1
account required pam_unix_account.so.1
account required pam_tsol_account.so.1
Default definition for Session management
Used when service name is not explicitly mentioned for session management
session definitive pam_user_policy.so.1
session required pam_unix_session.so.1
Default definition for Password management
Used when service name is not explicitly mentioned for password management
password definitive pam_user_policy.so.1
Password construction requirements apply to all users.
Edit /usr/lib/security/pam_authtok_common and remove force_check
to have the traditional authorized administrator bypass of construction
requirements.
password include pam_authtok_common
password required pam_authtok_store.so.1
password required pam_smb_passwd.so.1 nowarn
|
Done. Now, confirm that everything is working. On the second machine (solaris11-2), look up the first machine:
|
root@solaris11-2:/mnt# smbadm lookup-server //solaris11-1
Workgroup: WORKGROUP
Server: SOLARIS11-1
IP address: 192.168.1.103
|
And then we can verify which shares are available:
|
root@solaris11-2:/mnt# smbadm show-shares -u borges solaris11-1
Enter password:
c$ Default Share
IPC$ Remote IPC
smb_example_1
smb_example_2
4 shares (total=4, read=4)
|
Mount the first ZFS share (smb_example_1) from machine solaris11-1 onto machine solaris11-2:
|
root@solaris11-2:~# mount -o user=borges -F smbfs //solaris11-1/smb_example_1 /mnt
root@solaris11-2:~# **df -h /mnt
**Filesystem Size Used Available Capacity Mounted on
//solaris11-1/smb_example_1
40G 63M 40G 1% /mnt
root@solaris11-2:~# cd /mnt
root@solaris11-2:/mnt# ls -al
total 7414
drwxr-x---+ 1 2147483649 2147483650 512 Dec 5 16:35 .
drwxr-xr-x 31 root staff 33 Dec 5 13:43 ..
drwxr-x---+ 1 2147483649 2147483650 512 Dec 5 16:35 john-1.7.9-jumbo-7-Solaris-x86-64
-rwxr-----+ 1 2147483649 2147483650 3563461 Dec 5 16:35 john-1.7.9-jumbo-7-Solaris-x86-64-1.tar.gz
drwxr-x---+ 1 2147483649 2147483650 512 Dec 5 16:35 john_the_ripper
drwxr-x---+ 1 2147483649 2147483650 512 Dec 5 16:35 mhvtl-1.4
-rwxr-----+ 1 2147483649 2147483650 230896 Dec 5 16:35 mhvtl-2013-10-20.tgz
|
Now, instead of mounting the second SMB share (smb_example_2) onto solaris11-2 using the Oracle Solaris 11.1 command line, let's accomplish this task using Microsoft Windows.
For example, if you are running Microsoft Windows 7, you can search for ZFS shares by clicking the Windows Start icon and typing \\192.168.1.103 into the search box, as shown in Figure 1:

Figure 1. Searching for ZFS shares
As soon as you press Enter, all shares provided by machine solaris11-1 are shown. See Figure 2.
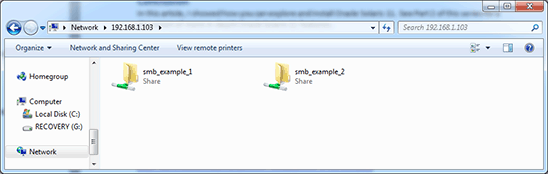
Figure 2. Currently available ZFS shares
Double-click the smb_example_2 folder to see the content of the smb_example_2 share:
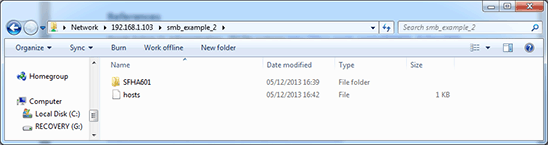
Figure 3. Content of smb_example_2 ZFS share
It worked! And, in case you didn't notice, no password was required because of the guestok=true setting that we configured for this second SMB share. If we had used the same procedure we used with the first SMB share (smb_example_1), we would have been asked for the username (Workgroup\borges) and the user's password.
Finally, unsharing is done by executing the following:
|
root@solaris11-1:~# zfs share.smb=off rpool/smb_example_1
root@solaris11-1:~# share
IPC$ smb - Remote IPC
c$ /var/smb/cvol smb - Default Share
smb_example_2 /rpool/smb_example_2 smb csc=auto,guestok=true
root@solaris11-1:~# zfs get share
NAME PROPERTY VALUE SOURCE
rpool/smb_example_2 share name=smb_example_2,path=/rpool/smb_example_2,prot=smb,csc=
auto,guestok=true local
|
See Also
Here are some links to other things I've written:
And here are some Oracle Solaris 11 resources:
About the Author
@"Alexandre Borges" is an Oracle ACE in Solaris and has been teaching courses on Oracle Solaris since 2001. He worked as an employee and a contracted instructor at Sun Microsystems, Inc. until 2010, teaching hundreds of courses on Oracle Solaris (such as Administration, Networking, DTrace, and ZFS), Oracle Solaris Performance Analysis, Oracle Solaris Security, Oracle Cluster Server, Oracle/Sun hardware, Java Enterprise System, MySQL Administration, MySQL Developer, MySQL Cluster, and MySQL tuning. He was awarded the title of Instructor of the Year twice for his performance teaching Sun Microsystems courses. Since 2009, he has been imparting training at Symantec Corporation (NetBackup, Symantec Cluster Server, Storage Foundation, and Backup Exec) and EC-Council [Certified Ethical Hacking (CEH)]. In addition, he has been working as a freelance instructor for Oracle education partners since 2010. In 2014, he became an instructor for Hitachi Data Systems (HDS) and Brocade.
Currently, he also teaches courses on Reverse Engineering, Windows Debugging, Memory Forensic Analysis, Assembly, Digital Forensic Analysis, and Malware Analysis. Alexandre is also an (ISC)2 CISSP instructor and has been writing articles on the Oracle Technical Network (OTN) on a regular basis since 2013.
| Revision 1.1, 12/16/2014 |
Follow us:
Blog | Facebook | Twitter | YouTube