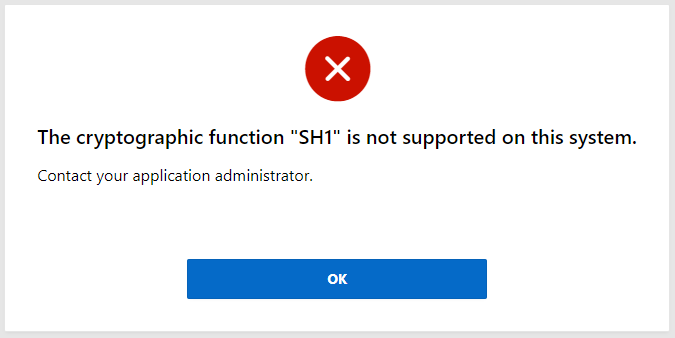
I am trying to set up a SAML authentication scenario in APEX 21.2 using Pulse Connect Secure as my identity provider (IdP). When accessing the application, I see the expected SAML request and response with assertion; however, I get the following error:
 The exported html of the debug messages is attached.
The exported html of the debug messages is attached.
Debug Message Data.txt (13.92 KB)