I deployed Oracle NoSQL Database CE on Minikube using this image: oracle/nosql:19.5-ce [https://github.com/oracle/docker-images/tree/main/NoSQL]
I followed this doc to make the db secure: https://docs.oracle.com/en/database/other-databases/nosql-database/19.5/security/single-node-secure-deployment.html#GUID-03A2067A-64CD-4CF4-99DC-D430DA8FD290
In the 3rd step, I used -pwdfile option since my db is CE version.
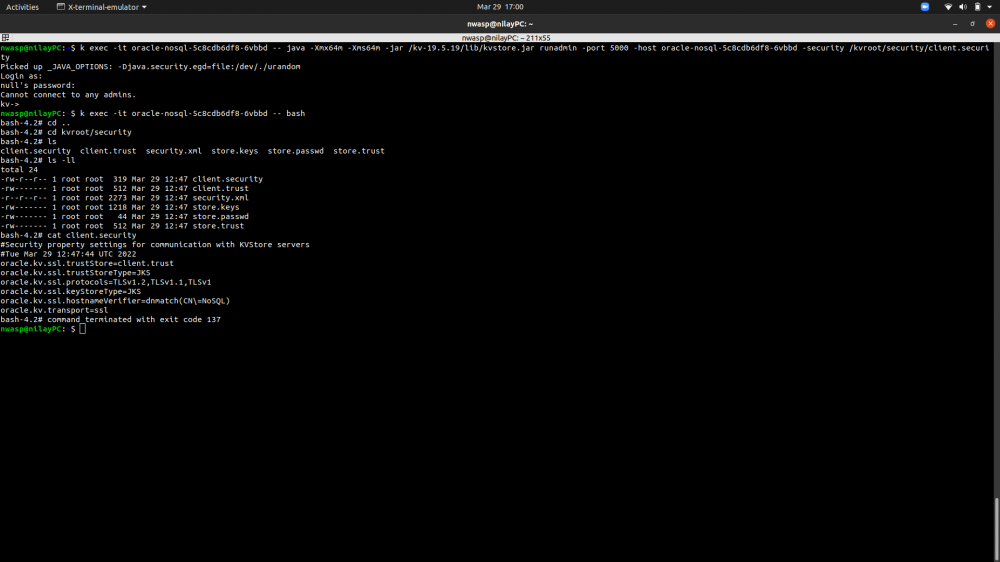
However, in the 7th step of this doc, I could not log in admin as anonymous as it should be. Instead, I was asked to provide a username and a password as you can see in the picture below:
 My Oracle NoSQL Database deployment and service yaml:
My Oracle NoSQL Database deployment and service yaml:
oracleNosql-deployment.yaml (0 Bytes)
So, what is that I am missing here?