Categories
- All Categories
- Oracle Analytics and AI Learning Hub
- 44 Oracle Analytics and AI Sharing Center
- 20 Oracle Analytics and AI Lounge
- 278 Oracle Analytics and AI News
- 56 Oracle Analytics and AI Videos
- 16.2K Oracle Analytics and AI Forums
- 6.4K Oracle Analytics and AI Labs
- Oracle Analytics and AI User Groups
- 103 Oracle Analytics and AI Trainings
- 20 Oracle Analytics and AI Challenge
- Find Partners
- For Partners
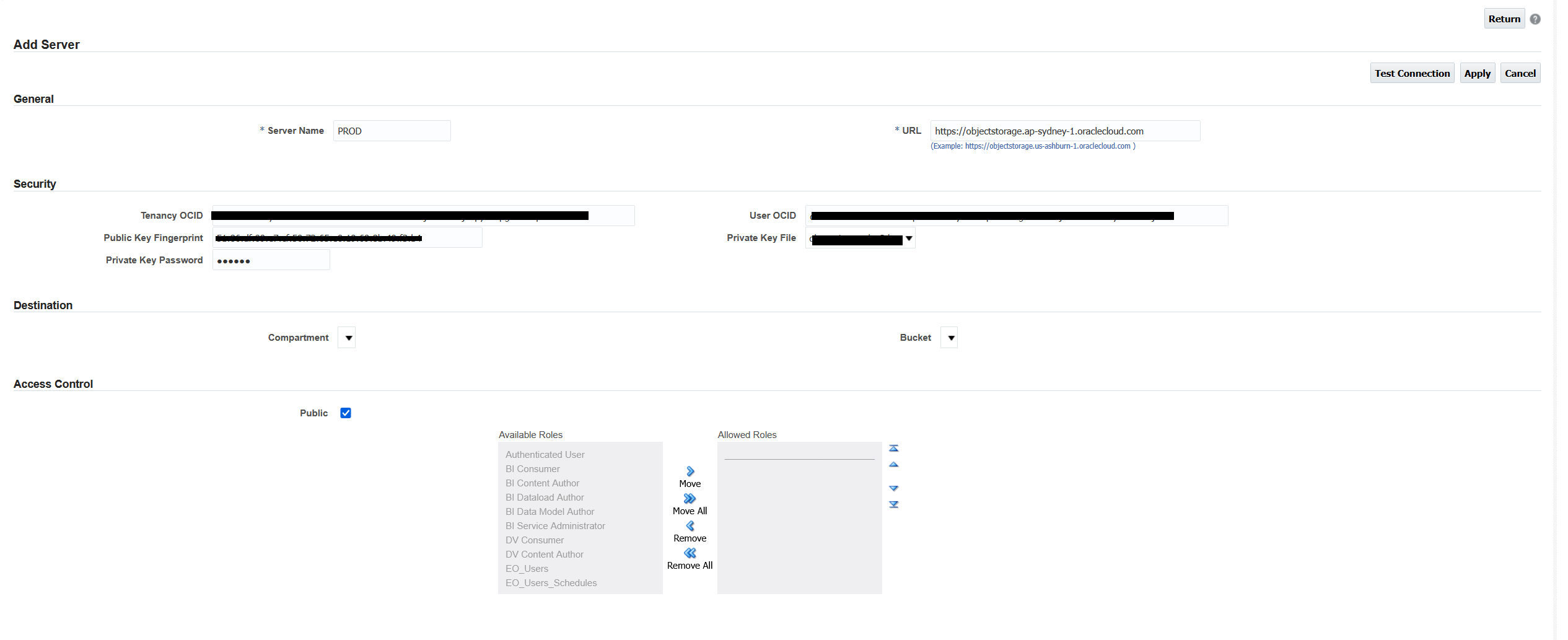
BI Publishing to Object Storage OCI Policies

Hi Folks, I wonder ifany of you OCI gurus have found a solution to my issue.
When I try to connect my BI publisher Delivery to Object storage using the documentation and recommendations for policies I still can't see compartments or buckets
Doc: https://docs.oracle.com/en/cloud/paas/analytics-cloud/acabi/add-object-storage.html
I get the below
I tried the suggested
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to inspect compartments in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to read objectstorage-namespaces in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to manage object-family in compartment 'comp-dev3' where any {request.operation='ListBuckets',request.operation='ListObjects',request.operation='PutObject',request.operation='GetObject',request.operation='CreateMultipartUpload',request.operation='UploadPart',request.operation='CommitMultipartUpload',request.operation='AbortMultipartUpload',request.operation='ListMultipartUploads',request.operation='ListMultipartUploadParts',request.operation='HeadObject',request.operation='DeleteObject'}
I even tried opening further
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to manage buckets in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to manage objects in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to read objectstorage-namespaces in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to inspect compartments in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to inspect buckets in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to read buckets in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to manage objects in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to manage all-resources in tenancy
Allow group 'OracleIdentityCloudService'/'DEV3_OACS_Admins' to MANAGE OBJECT-FAMILY in tenancy
However still no joy unless I make the user a member of the OCI Administrators group (which is not best practice or meets least privilege policies)
Please share your thoughts as an SR has not helped resolve this, but highlighted its an issue in Fusion too.
Answers
-
This was was another policy conflicting however the correct syntax was
Allow group 'OracleIdentityCloudService'/'GROUP_NAME' to inspect all-resources in tenancy
Allow group 'OracleIdentityCloudService'/'GROUP_NAME' to inspect compartments in tenancy
Allow group 'OracleIdentityCloudService'/'GROUP_NAME' to read objectstorage-namespaces in tenancy
Allow group 'OracleIdentityCloudService'/'GROUP_NAME' to manage object-family in compartment 'COMPARTMENT' where any {request.operation='ListBuckets',request.operation='ListObjects',request.operation='PutObject',request.operation='GetObject',request.operation='CreateMultipartUpload',request.operation='UploadPart',request.operation='CommitMultipartUpload',request.operation='AbortMultipartUpload',request.operation='ListMultipartUploads',request.operation='ListMultipartUploadParts',request.operation='HeadObject',request.operation='DeleteObject'}
0 -
@Melanie' , Thanks for sharing this interesting post. Looking at the comments, I believe Granting "inspect all-resources in tenancy" is technically required, low risk, and compliant with least-privilege principles for enabling BI Publisher Object Storage delivery in Oracle Analytics Cloud.
0