Categories
- All Categories
- Oracle Analytics and AI Learning Hub
- 48 Oracle Analytics and AI Sharing Center
- 19 Oracle Analytics and AI Lounge
- 286 Oracle Analytics and AI News
- 57 Oracle Analytics and AI Videos
- 16.3K Oracle Analytics and AI Forums
- 6.4K Oracle Analytics and AI Labs
- Oracle Analytics and AI User Groups
- 110 Oracle Analytics and AI Trainings
- 20 Oracle Analytics and AI Challenge
- Find Partners
- For Partners
OAS DV embedding - Access to font has been blocked by by CORS policy
Answers
-
I think you need to engage whoever manages sandbox.pc.com, do they have a webserver and can they set headers? There will be additional things that need to be set after you clear the first blocker with the fonts mentioned above.
If sandbox.com or devbi can use an F5 it can be done at that layer, see something like: https://community.f5.com/discussions/technicalforum/access-control-allow-origin-on-f5/54171
0 -
Thank you. I tried both things but no luck.
I had also tried adding the FilesMatch in httpd.conf and ssl.conf.
Other files (.gif, .css, .js) do not get this issue.
For example:
https://bidev.pc.com/dv/static/obitech-common/0.1.0.03a5a3897475/images/redwood_progress.gif (200 OK)
The Location in the Response Headers for .woff and .ttf files is https://sandbox.pc.com/saml-sso?SAMLRequest=fZFba4NAEIX%2Fiuy7……. as if it cannot get the SAML session; Status Code is 302. Whereas other files get 200.
0 -
When getting a 200 OK, it may simply mean that is not subject to CORS. Due to it not crossing origins. When you provided the blocked get request, we can see its crossing origins from sandbox.pc.com to bidev.pc.com as I show below. It also shows the referrer. If you provide the successful request info similar to below it may better inform us why the .woff fails.
For the successful font request & blocked woff requests please share more details including:
-Request headers
-Response headers
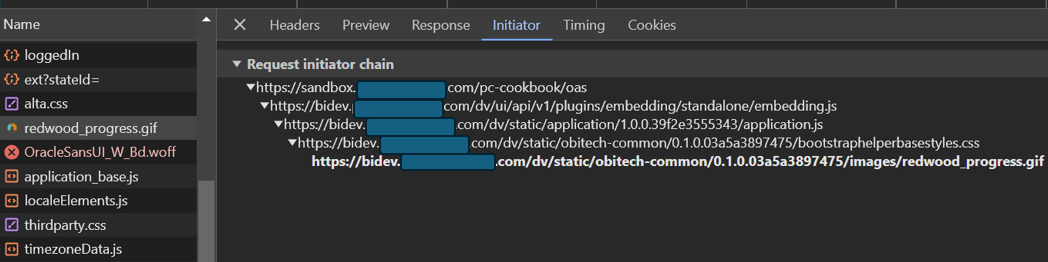
-Initiator chain eg:
0 -
Successful .gif
Request Headers
GET /dv/static/obitech-common/0.1.0.03a5a3897475/images/redwood_progress.gif HTTP/1.1
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Accept-Encoding: gzip, deflate, br, zstd Accept-Language: en-US,en;q=0.9
Connection: keep-alive
Cookie: JSESSIONID=K73X9xBZw_lT-3kYTHMInlayIOmB39czuPuX6-5do087mHTUHaW7!7565341; _WL_AUTHCOOKIE_JSESSIONID=DBtO7.byFVQSMabAi.Tc; BIGipServerBIDEV.PC.COM_POOL_6443=!VhVlZNeqASOWxiU7LFMgJbLrG7tgBoWrHf6xgSmjtZZdBrcuPRYrOUzj51MhOAxIIO2OOA27SDpfQw==; _gid=GA1.2.1336555533.1738790036; _gat_UA-30325608-8=1; _sfid_a769={%22anonymousId%22:%225570374727a127d2%22%2C%22consents%22:[]}; _ga=GA1.2.1537657441.1738790036; _evga_2def={%22uuid%22:%225570374727a127d2%22%2C%22puid%22:%22GVdFDxSWpmJIngemjfeMd3wvL0rOPi62vkjkOYvxqQMmmjlaBcMf9FB7O09G6DpOAE8bbVXPuR38gFGvON_Ea6EXyA8ruBQJ_fYFE21xjmo%22%2C%22affinityId%22:%2201K%22}; _ga_2LL237F0ZT=GS1.1.1738790036.1.0.1738790044.0.0.0; _shibsession_bidev=_ad55a2fc40d31755719980d2884f7e04
Host: bidev.pc.com
Referer: https://bidev.pc.com/dv/static/obitech-common/0.1.0.03a5a3897475/bootstraphelperbasestyles.css
Sec-Fetch-Dest: image
Sec-Fetch-Mode: no-cors
Sec-Fetch-Site: same-site
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
sec-ch-ua: "Not A(Brand";v="8", "Chromium";v="132", "Google Chrome";v="132"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Response Headers
HTTP/1.1 200 OK
Date: Wed, 05 Feb 2025 21:14:53 GMT
Server: Apache
Strict-Transport-Security: max-age=63072000; includeSubdomains
Cache-Control: public
Content-Type: image/gif
X-ORACLE-DMS-ECID: b49ae8a8-7651-47c5-9738-3dc0d33a6096-00000708
X-ORACLE-DMS-RID: 0
Vary: Origin,X-Forwarded-Proto,WL-Proxy-SSL
Expires: Wed, 04 Feb 2026 21:14:53 GMT
Strict-Transport-Security: max-age=31536000; includeSubdomains
Keep-Alive: timeout=5, max=95 Connection:
Keep-Alive Transfer-Encoding: chunked
Initiator Chain:
Blocked .woff
Request Headers
GET /dv/static/application/1.0.0.39f2e3555343/obitech-application/fonts/OracleSansUI_W_Bd.woff HTTP/1.1
Accept: */* Accept-Encoding: gzip, deflate, br, zstd
Accept-Language: en-US,en;q=0.9
Connection: keep-alive
Host: bidev.pc.com
Origin:
Referer: https://bidev.pc.com/dv/static/application/1.0.0.39f2e3555343/application.css
Sec-Fetch-Dest: font
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-site
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36
sec-ch-ua: "Not A(Brand";v="8", "Chromium";v="132", "Google Chrome";v="132"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Response Headers
HTTP/1.1 302 Found
Date: Wed, 05 Feb 2025 21:14:53 GMT Server: Apache
Strict-Transport-Security: max-age=63072000; includeSubdomains
Set-Cookie: _opensaml_req_ss%3Amem%3Aee330b6b05c0de956ad9fcc27a07376338f4821689f06db1383ef2680fce6986=_419cf35c7cdbde11e1f83c9d014835fb; path=/; secure; HttpOnly; SameSite=None
Expires: Wed, 01 Jan 1997 12:00:00 GMT
Cache-Control: private,no-store,no-cache,max-age=0
Location: https://sandbox.pc.com/saml-sso?SAMLRequest=fZFbT4NAEIX%2FCtn3cmuJ..WkoA%2B%2BmGUZZB...5NLQ%2Fw3gMa69Q2EullEJ...cWJvBjpDsDP7FIJNloU7%2FQWfHkwFBrGQTkteZt%2BDVNOB3...GSRMS3%2FWDietP3CD3Pe.XElZCnk2%2B1CilGE9..5bC%2BK..klVI%2FinFTeN%2B..Glf%2B%2Fjr6Ag%3D%3D&RelayState=ss%3Amem%3Ae..86&SigAlg=http%3A%2F%2Fwww.w3.org%2F2001%2F04%2Fxmldsig-more%23rsa-sha256&Signature=GjjYeC...D0d0%2FqXOJX%2BKMUw1jA%2FK%2B%...Q%2F8FOEtC%2B1..4x%2B...A%2BV...ip%2F..p0%2B...sg%3D%3D
Content-Length: 1239
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
Set-Cookie: BIGipServerBIDEV.PC.COM_POOL_6443=!MQ3Rllmn/0VWYmg7LFMgJbLrG7tgBrOVBe3tRqRYXLFMAirKmYYKE4hhGubl6d+WtShup2RpjtCWsQ==; path=/; Httponly; Secure
Initiator Chain
0 -
Sec-Fetch-Mode: - this is set as "no-cors" for .gif and "cors" from .woff.
Where is this value set? Would it be the weblogic application which has the .woff file?
And other files like .css (https://bidev.pc.com/dv/static/oracle-jet/11.1.10.39f2e3555343/ojs/styles/alta/alta.css) have
sec-fetch-mode:corsbut also have
access-control-allow-origin:https://sandbox.pc.com set in Response Headers, so they are not blocked.0 -
Hi Rav,
I agree with you about the .css file, and the root cause assessment about the auth for the static files being blocked.
I am glad you found a solution.
(btw, you may want to edit one of your posts where you exposed your real host name ;-))I know we proposed some potential solutions based on the limited information.
These solutions generally are specific to the architecture.
For example, I proposed a potential .htaccess / virtual host
Other potential possibilities could include.
This allows Access-Control-Allow-Origin only for the allowed matched domain and subdomains<IfModule mod_headers.c> SetEnvIf Origin "https://(www|sub1|sub2|sub3).domain.com$" ACAO=$0 Header set Access-Control-Allow-Origin "%{ACAO}e" env=ACAO Header set Access-Control-Allow-Methods "GET" </IfModule>For future readers, there may not be a "one size fits all" type solution.
I will make your solution, as 'answered' for this thread.
3